Country to Country (C2C) CTF Write-Up Part 1
- Tejas Walke
- Feb 24, 2025
- 6 min read
Updated: May 25, 2025
Husky Hunt

Solution:
I identified that the text was in Base64 format.
I decoded it using a standard Base64 decoder.
After decoding, I took the first word from the output as the flag.
Flag: KRENTZMAN

Paws Hideout

Solution:
Step 1: Extracting the ZIP File
I downloaded and extracted the Paws_Hideout.zip file, which contained a text file named directions.
Step 2: Inspecting the File Contents
I used the cat command to view the contents:
cat directionsThe output contained repeated sequences of the words "up" and "down", such as:
up down up up up down down up down up up up...
Step 3: Recognizing a Binary Pattern
Observing the pattern, I realized that "up" and "down" could represent binary digits (0s and 1s). I made the following assumption for conversion:
up → 0
down → 1
Using a text editor with find-and-replace functionality, I replaced "up" with 1 and "down" with 0, obtaining a binary string.


Step 4: Converting Binary to Text (ASCII/UTF-8)
The binary string was then converted to readable text using an online binary-to-text converter with ASCII/UTF-8 encoding.

Step 5: Extracting the Flag
Upon conversion, the output revealed the flag:
Flag: C2C_CTF{binary_substitution_for_da_win}
Husky Hash

Solution:
Step 1: Extracting the First ZIP File
I downloaded and extracted Husky_Hash.zip, which contained:
passwd (a hashed password file)
wordlist.txt (a list of potential passwords)
flag.zip (a second password-protected ZIP file)

Step 2: Cracking the Password with John the Ripper
Since the passwd file contained a hash, I used John the Ripper to crack it:
john --wordlist=words.txt --format=md5crypt passwdAfter running the command, John successfully cracked the hash and revealed the password: 📌 Password: husky
Step 3: Extracting flag.zip
Using the password, I extracted flag.zip
unzip -P husky flag.zipThis extracted an image file.

Step 4: Analyzing the Image (Birds-On-A-Wire Cipher)
The extracted image showed silhouettes of birds sitting on a wire, which looked like a cipher.
I recognized it as the Birds-On-A-Wire cipher, a pictographic substitution cipher where each unique bird position represents a letter.
I used the provided Birds-On-A-Wire cipher translation table to decode the bird positions into letters.
Step 5: Extracting the Flag
By carefully translating each bird's position, I obtained the plaintext:
Flag: HOWLINGHUSKIE
Picture Game

Solution:
Step 1: Observing the Image

When I opened the provided image, I noticed:
A traditional Japanese shrine with a red roof.
A distinct banner with a black-and-white symbol in the center.
And the Japan flag all over the image :p
At this point, I was confident that the image was taken somewhere in Japan, but I needed to narrow down the location.
Step 2: Identifying Key Features
Analyzing the Black-and-White Symbol
One of the most distinctive features was the black-and-white symbol on the banner. It looked circular with three curved sections, resembling a shuriken (throwing star) or a swirling pattern.
To investigate further, I:
Took a screenshot of the symbol.
Used Google Lens to perform a reverse image search, but I didn’t get immediate results.
Then, I manually searched Google using terms like:"Japanese shrine black and white symbol""Japanese temple swirl symbol"
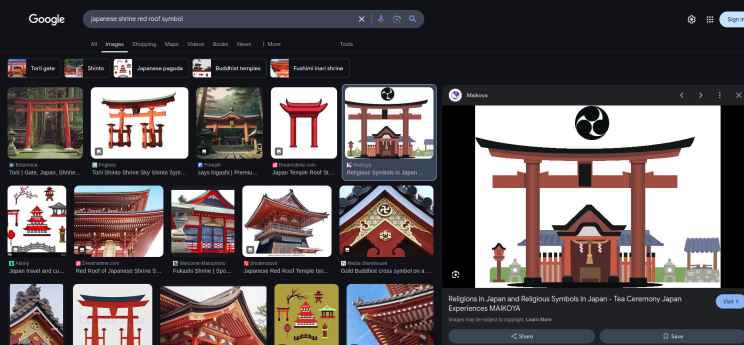
This led me to a symbol known as Tomoe (巴), particularly the Mitsu-Domoe (三つ巴), which consists of three comma-like shapes forming a swirl.

Step 3: Understanding the Symbol - Mitsu-Domoe
Now that I had identified the symbol as Mitsu-Domoe, I needed to find where it was commonly used.
From my research, I learned:
Mitsu-Domoe is associated with Shinto shrines and samurai culture.
It is often seen on shrine banners, drums, and roof tiles.
The symbol is believed to represent the elements of earth, sky, and water, and it is widely used in Okinawan religious sites.


This meant I had to focus on Shinto shrines in Japan, particularly in Okinawa.
Step 4: Searching for a Shrine with Mitsu-Domoe
With this information, I refined my Google search to:
"Japanese shrine Mitsu-Domoe symbol"
"Okinawa Shinto shrine red roof"
This led me to Naminoue Shrine, a famous Shinto shrine in Naha, Okinawa.
To confirm, I compared images of Naminoue Shrine with the CTF image and found a perfect match: ✅ The red roof ✅ The banners with Mitsu-Domoe ✅ The Japanese flags with similar text.

Step 5: Formatting and Submitting the Flag
The challenge specified the flag format as: C2C_CTF{Something_Something_City}
From my findings, the shrine’s full name and location were:
Naminoue Shrine (神社)
Located in Naha, Okinawa, Japan
Thus, the correct flag submission was:
Flag: C2C_CTF{Naminoue_Shinto_Naha}
Unknown File Type

Solution:
Step 1: Extracting the ZIP File
I downloaded the Forensics-SuperEasy.zip file and extracted its contents. Inside the folder, I found:
Forensics-SuperEasy.zip (which I had already extracted)
OSINT-SuperEasy.gb
The .gb file extension immediately caught my attention, as .gb files are associated with Game Boy ROMs.

Step 2: Identifying the File Type
To confirm the file type, I used the file command in Linux:
file OSINT-SuperEasy.gbThe output verified that it was indeed a Game Boy ROM. Since ROMs are executable game files, the next logical step was to run the ROM in an emulator.
Step 3: Running the Game Boy ROM
To run the ROM, I needed a Game Boy emulator. I installed VisualBoyAdvance, a popular emulator for playing Game Boy games, using:
sudo apt install visualboyadvance
After installation, I launched the ROM with:
visualboyadvance OSINT-SuperEasy.gb
Step 4: Extracting the Flag
Once the emulator opened, I was greeted with a black screen displaying “C2C - CTF” and a prompt saying "Press Start".
I pressed Enter (which functions as the Start button in the emulator), and after navigating the game, the flag was revealed on the screen:

HuskySniff

Solution:
Step 1: Identifying the File Type
The file had no extension, so the first step was to check what kind of file it was.
I used the file command in Linux:
file huskysniffThe output showed that it was an ELF (Executable and Linkable Format) binary, meaning it was an executable file for Linux.
To further confirm, I uploaded the file to an online file type checker, which also identified it as an ELF 64-bit dynamically linked executable.

Step 2: Running the Binary Analysis
Since the file was an executable, I ran it using
./huskysniffThis produced a text output, hinting some clue, so I ran the strings command using
strings huskysniffThis produced a huge amount of text output, so I decided to filter it for anything relevant by looking for c2c or ctf, as flags often follow a recognizable pattern.


Step 3: Extracting the Flag
To efficiently find the flag, I used:
strings huskysniff > husky.txtThis created a txt file with the output from the strings command being copied to the txt file. Then I opened the created txt file with command output and searched for "c2c" and voila!

Husky Walk

Step 1: Identifying the File
After downloading the file huskywalk, I noticed it had no extension. To determine its type, I ran the file command:
file huskywalkThe output confirmed that it was an ELF 64-bit executable, meaning it was a Linux binary.
Step 2: Running the Executable
Before running any unknown binary, it's always good practice to check for potential malicious behavior. Since this was a CTF challenge, I decided to execute it in a controlled environment.
I first made the file executable using:
chmod +x huskywalkThen, I ran it:
./huskywalkThe program displayed a message:
Hey hooman! Can we pleaaase go to the park? I wanna run super fast, sniff all the things, and maybe make some new furry friends! Pretty please with extra belly rubs? Which park are we going to?!
It seemed like the program was expecting some input.
Step 3: Finding Clues
I tried entering random inputs, but the program responded with:
Umm, hooman… not that park! It’s boring, no good sniffs, and no fun friends to play with! Can we go somewhere way more exciting instead? Pleaaase?Since guessing the correct input blindly wasn't efficient, I needed to analyze the binary for hidden clues.
Step 4: Extracting Hidden Strings
To find useful hints, I used the strings command, which extracts readable text from binary files:
strings
huskywalk > walk.txtThis saved the output to a text file named walk.txt.

Next, I opened the file and searched for "c2c" and found the flag!
Husky Play
Solution:
The same ELF process I mentioned earlier,
Determine Filetype
Ran the file using ./
Got some clue
Copied the strings output to a txt file and searched for c2c.

However, I couldn't find anything with "c2c", so I started analyzing the contents in depth. And found a phrase that had relevancy with the earlier flag format, just not "c2c".

It had y2y_ypb which is a strong indication of Caesar's Cipher. So I ran it and voila! Got the Flag!

There is a Part 2, but I will post that in a few days!
This was the qualifier round, and I’ve made it to the finals! The in-person event will be held at Northeastern University from July 6-10, and I couldn’t be more excited!
The C2C CTF Qualifier Round was incredible, with each challenge offering a valuable learning experience. I secured 81st place globally, earning 2360 points, and I'm eagerly looking forward to competing in the finals!
